
The eDiscovery Checklist Manifesto is
From the moment litigation becomes imminent until a settlement or judgment, practitioners in e-discovery cannot afford to miss anything. It is crucial to both meet the necessary legal requirements to the court and zealously represent your client while at the same time managing time, budget, and risk.
Add the free checklist to your toolkit and make sure you and your team have every step in the eDiscovery process covered.
A one hour ACEDs webinar discussing the Checklist Manifesto is available below, as well as a previous version of the Manifesto targeted towards Digital WarRoom users.

eDiscovery Checklist Manifesto Webinar

eDiscovery Checklist Manifesto Written by:
Tom O'Connor - Litigation Technology Consultant at Gulf Coast Legal Technology
Bill Gallivan - Managing Director at Digital WarRoom.
Litigation is complex, dynamic, and unpredictable. A good checklist is designed to be your guide book in forming a consistent, repeatable process. From the moment litigation becomes imminent until a settlement or judgment - you cannot afford to miss anything. Because of the high stakes of litigation, it is crucial that you meet your requirements to the court and that you justly represent your client while managing time, budget and risk. This manifesto will serve as a complete eDiscovery litigation checklist covering the entire legal discovery process.
The traditional Electronic Discovery Reference Model (EDRM) was developed in 2005 to provide litigators with common language and baseline steps for which to evaluate service providers. While the EDRM is still useful, the industry has matured.
What has changed since 2005?
1) It no longer takes a collection of teams and experts to navigate eDiscovery
2) DIY eDiscovery is now available at affordable rates for small and medium sized litigation
3) Attorneys are now expected to be technologically educated on issues relating to eDiscovery
Because of the advances listed above, the cost of litigation has dropped significantly and the job description of a litigator has expanded. Educational content must evolve to encompass the newfound technological requirements of litigators in alignment with their traditional role of risk management, cost management and time management. Digital WarRoom recognizes that all of these responsibilities constitute an iterative, nonlinear process. In this checklist, we establish a complete list of points which form a more accurate depiction of the workflow of the modern day litigator.
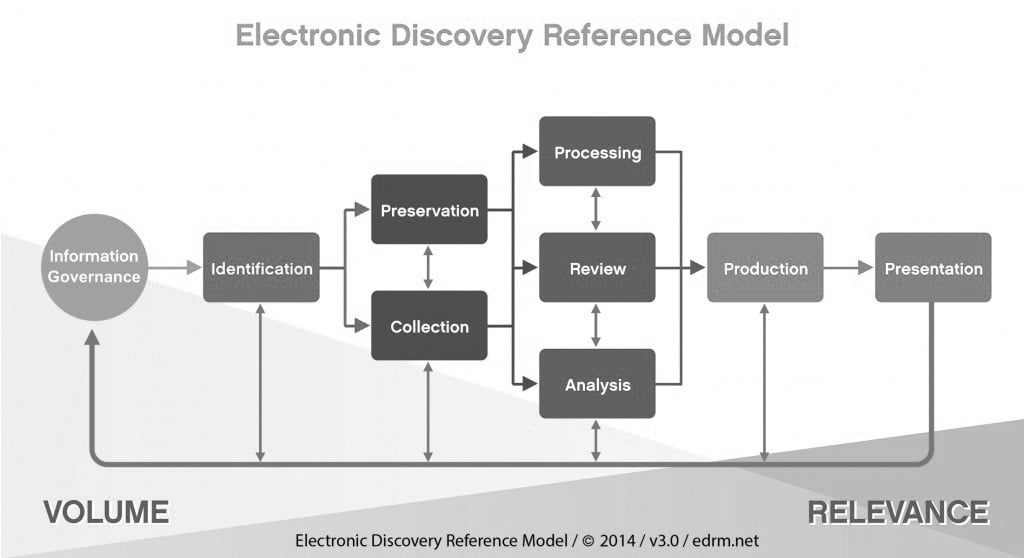
The EDRM model, originally designed by George Socha and Tom Gelbmann and now owned by the Duke University Law School, is intended as a basis for discussion and analysis of the eDiscovery process. The EDRM is defined as a framework for approaching the e discovery process.
Our diagram shown below, is based in part on the EDRM diagram. The outer circle represents unique steps while the inner circle represents more common steps which may occur at any
point in the process. Like the EDRM chart, this is not a literal, linear or waterfall model. The ordering of the stages are only important conceptually. In reality, you can cycle back to earlier steps at any time, refining your approach as you gain a better understanding of the data or as the nature of your matter changes. The diagram is intended for discussion purposes, not as a prescription for the one and only right way to approach the eDiscovery process flow.
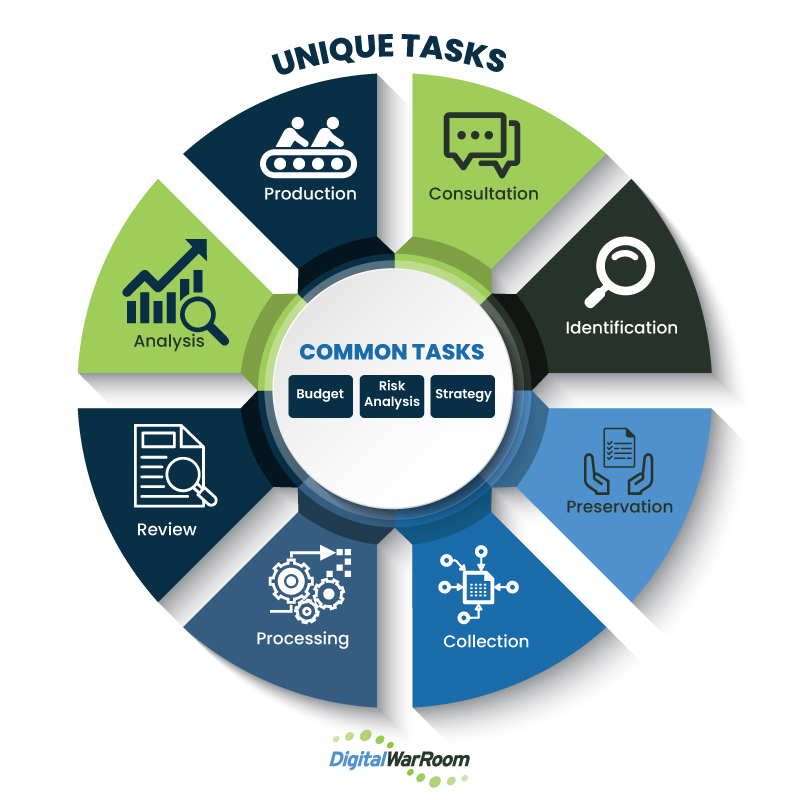
Given this context, all stages outlined in the diagram should be considered at one or multiple points as you move through litigation. The goal of our checklist manifesto is to include a high level checklist associated with each stage. Because of the intended simplicity, we recommend that you consider every bullet. Throughout the document, we will link to more specific and detailed information. At that point it is up to you to decide your level of granularity.
eDiscovery Requirements & Obligations: Relevant rules and standards for attorneys
Client Interview: Consider and discuss these points in the initial client meetings
Identification: Identify and validate all potentially relevant ESI sources
Preservation: Issue litigation holds and stop the unintended destruction of potentially relevant ESI or associated metadata
Custodian Interviews: Get in contact with system administrators who may be relevant to the litigation
Collection: Acquire potentially relevant ESI in a forensically sound manner
Processing: Prepare ESI for filtering, analysis and review by storing metadata, indexing text,
etc.
Metadata: Explore types of metadata which may play a role in electronic discovery
Early Case Assessment: Begin to understand your data as it relates to the case in order to make reasonable agreements with the opposing party during the ongoing 26 f conference
Review: Make decisions on each document for disclosure and claim construction using tools such as filtering and keyword search.
Analysis: Examine trends in your data set using early case assessment tools in concordance with your risk and budget management strategies
Production: Disclose ESI relevant to the investigation in agreed-upon formats while not producing privileged documents
Strategy: Create a comprehensive game plan for controlling your litigation
Risk Analysis: Consider liabilities, requirements, sanctions and business impact
Budget: Understand contemplated costs and assess if damage is proportional to the burden of litigation and eDiscovery
These are issues every attorney should be aware of and conversant with themselves.
Rule 1: Just, Speedy, and Inexpensive
Rule 26 (b) (1) - Scope and Proportionality (Link)
Rule 26(f)- Meet and Confer Conference of the Parties (Link)
Rule 34 - Form of Production and Specificity (Link)
ABA Model Rule 1.1 has been adopted by 34 of the states and proscribes a mandatory ethical duty of technological competence (Link)
State Bar CLE Requirements. (Link)
These are consultation points that every attorney should cover or consider in the initial discussion with the client. This interview should provide insight for other EDRM steps such as Identification, Preservation, and Collection. Consultation can occur at any time and should occur before any specific litigation in order to adequately prepare the client in a proactive manner for issue that may arise should litigation occur. Consultation may then occur cyclically throughout any project and will flow into the Strategy checklist set out further below.
Consider these points when litigation becomes imminent
Business Type: What is the business type?
Business Specific Practices: Are there specific document types, technology and/or training of personnel common to the client’s business and the employees who will be involved in this discussion?
Data Management Questions: What is the current data management strategy? Does the client have any formal data retention policies and procedures? If so, what is it and what tools are used? If not, how do employees save, retrieve and share documents?
Information Governance Considerations: What are the information governance (IG) policies and procedures? What are the document management systems (DMS)?
Legal Preservation Requirements: What documents fall under a legal requirement such as HIPPA, banking, privacy regulations, insurance, etc?
Data Map: Does the IT department keep a data map? If not, they should. The data map is also related to org chart
Employee Chart: You will need a complete employee organizational (org) chart with name, positions, business locations; all linked to the data map.
Privacy Considerations: You will need to cover privacy considerations with HR people and discuss any and all document retention areas where privacy issues may apply.
Insurance Considerations: Gather copies of all Insurance Coverage(s) including policies and analysis of coverage for disputes that may arise. Don’t forget policies on individuals including life insurance policies that may have E/O or DI coverage.
A lawyer cannot provide a specific budget or pricing until the items in this checklist are considered and agreed upon. Wrap your checklist conclusions into a timeline with action items and Project Management items from the Strategy section. For a good overview discussion of Project Management, listen to Mike Quartararo on Youtube or visit his website.
In the EDRM, the legal team uses the identification phase to identify and validate potentially relevant sources of ESI which could include people and systems. One common way to do this is by creating an ESI data map. This information will be crucial to issue an effective litigation hold in the Preservation stage. The scope of potentially relevant data may be uncertain in the early phases of a legal dispute, so after you gather insight from the initial client consultation and custodian interviews, the next step is figuring out where to look.
A successful electronic discovery project must include an accurate picture of the target company’s data sources. The data map will consist of all hardware and software deployed to accomplish routine tasks such as managing company e-mail or creating data backups.
You may have to be creative to uncover all the information and data maps tend to vary widely from organization to organization and even within separate units of a sufficiently large individual company.
This identification process will locate servers of all types with data of all types (e.g. file servers, collaboration servers, e-mail servers, web servers, litigation servers) as well as any data management systems (e.g. document management systems, financial systems, disaster recovery, and backup systems).
Thus the map will cover servers with overall company data as well as user data such as user home directories or departmental shared directories. It should also include all BYOD (Bring Your Own Drive) sources such as laptops, tablets, smartphones, memory cards and access from home computers.
The underlying legal responsibility here is to isolate and protect against the intentional or unintentional destruction of potentially relevant data. This process must be reasonable; proportionate; efficient and auditable. The phrase often used by courts is that this should be a “repeatable, defensible process.”
The duty to preserve relevant data does not always flow from a litigation hold notice. It may arise under a common law obligation, a statute or regulation. In Federal court, the obligation arises when the party has received notice that the evidence is relevant to litigation OR when a party should have known that the evidence may be relevant to future litigation.
In the federal and most state courts, there is no tort cause of action for the intentional destruction of evidence after litigation has commenced. However, since such destruction constitutes the abuse of the discovery process, it is subject to a broad range of sanctions. These sanctions are intended to remedy discovery abuse rather than punish the offending party.
Finally, remember that the duty to preserve is not the same as the directive to produce. Theoretically, preservation is broad while production is more targeted. Begin with your strategy and work forward from there.
The EDRM defines a litigation hold as a “ … communication issued as a result of current or anticipated litigation, audit, government investigation or other such matter that suspends the normal disposition or processing of records. “ (Link)
Audit trail
See Pension Committee of the University of Montreal Pension Plan v. Banc of America Securities, LLC, 2010 WL 184312 (S.D.N.Y. Jan. 15, 2010) (Duty to preserve and relevant sanctions)
Identify and review all custodians and system administrators who may be relevant to the litigation. Simple and straightforward questions often elicit the most helpful answers and should be focused on the time frame and data questions at the center of the dispute.
Some areas to consider in an e discovery questionnaire include:
Collection is the acquisition of potentially relevant electronically stored information (ESI) as defined in the identification phase. The process of collecting ESI will generally provide feedback to the identification function which may then influence or even expand the scope of the ediscovery project.
Form Of Collection
.jpg?width=450&name=Collection%20(1).jpg)
Format Of The Data
Proportionality
Prove to the court that you collected data in an appropriate manner.
After collection, it is often necessary to “process” data to prepare it for review. The goals of processing are for the reviewer to first identify what is in the data set to develop a sense of the organizational  structure. When the documents are processed in an eDiscovery tool, all item-level metadata will be recorded as it existed prior to processing. To enable defensible reduction of data, the user can create initial filter criteria in the policy wizard such a relevant date range which will carry only appropriate items forward to the "review" view. (Link)
structure. When the documents are processed in an eDiscovery tool, all item-level metadata will be recorded as it existed prior to processing. To enable defensible reduction of data, the user can create initial filter criteria in the policy wizard such a relevant date range which will carry only appropriate items forward to the "review" view. (Link)
This wizard is also known as the “26f Wizard”. This is a way to create preliminary filters which quickly remove documents that are repetitive or outside the scope of the investigation. As both parties continue to define potentially relevant, you will be able to strengthen your eDiscovery policy, thereby reducing data volume and dramatically lowering ediscovery costs.
Metadata is "data [information] that provides information about other data". There are many types of metadata out there. You should know what data you were given, what data could be missing and how this information could help you.
Metadata is data created by the computer that the user does not see. As such, track changes comments are technically not metadata but it is often referred to as such and metadata such as vendor added blur that distinction.
Within an eDiscovery tool, open up the metadata selector window and decide which metadata is most relevant to view based on the types of documents that were collected. Different file extensions can have completely different metadata
Document review is where your team will likely spend most of their time during an eDiscovery project. The duty to preserve is not the same as the directive to produce. People tend to over-preserve out of an abundance of caution. During review, you will have the opportunity use your legal discovery software to cull down your data. In fact, in our opinion, the goal of early case assessment is to reduce data volume, lower costs and save time. Keep in mind that early case assessment occurs throughout the EDRM and ties in closely with the common steps included in our eDiscovery workflow infographic. The points mentioned in this “early case assessment” section can be completed continuously and in any order.
According to the FRCP, the plaintiff must initiate a conference between the parties to plan for the discovery process after the complaint was served to the defendants. ... The parties should attempt to agree on the proposed discovery plan, and submit it to the court within 14 days after the conference. For a good discussion of this practice area, see Chapter 6, Section of the Federal Practice Manual for Legal Aid attorneys.
At this point you should be well-equipped to start your review, Keep in mind that 60-70% of the total cost of an eDiscovery project will come during the review process due to both the hosting of data in a document review platform and from payroll and/or vendor service fees. It is crucial then to always keep in mind at the early stages of your project what the downstream costs will be in terms of review, including multiple levels of review, QC steps, QC personnel and additional post-production review for further case development.
This section is intentionally broad. Becoming an efficient reviewer has to do with the workflow and click stream of your particular software solution. This is not a how-to software guide, but keep in mind the following themes.
Some steps to consider during review in order to maximize savings and organize your data are:
In the original EDRM model, the term “Analyze” referred to the ongoing process of understanding your data. At that point in time, it was primarily a manual process and was mentioned in conjunction with early case assessment and also as a standard function of the Review process. But over time, more sophisticated analytics tools have emerged and this concept has drawn more attention as an ongoing way to increase productivity.
In contrast to the modular setup of the EDRM, we believe that you should take steps to understand your data at every step of your eDiscovery project. Rather than confining you to a specific workflow stage as the correct time to learn more about your data, we provide actionable steps so that you can develop a realistic mindset of continuously adjusting your expectations and refining your workflow.
These steps include:
The production of ESI continues to present significant challenges in the discovery process. FRCP Rule 26(f) posits that the method and format of production shall be included in the discovery plan. Be sure to specifically discuss preferred loadfile formats and test a sample set before proceeding to import a significant amount of data.
Production Protocol: Review your production protocol report from your 26(f) conference
A comprehensive strategy will be the single greatest factor in controlling your litigation. It should be dynamic, flexible and reviewed periodically.
During the eDiscovery process, you will need to balance eDiscovery cost with risk. To avoid the risk of sanctions, you will need to know your eDiscovery related requirements and put together the necessary budget to meet, and go behind those obligations.
General Considerations to Manage Risk
Know Your Requirements
Duty of Technology Competence
ABA Model Rule 1.1 has been adopted by 34 of the states and proscribes a mandatory ethical duty of competence.
Comment 8: To maintain the requisite knowledge and skill, a lawyer should keep abreast of changes in the law and its practice, including the benefits and risks associated with relevant technology, engage in continuing study and education and comply with all continuing legal education requirements to which the lawyer is subject.
Cost Vs Risk
Avoiding all possible costs and ignoring obligations may lead to sanctions. There is a minimum and reasonable set of costs required to meet obligations. More recently, these costs have decreased and eDiscovery has become more accessible for small and medium sized firms.
On the other hand, meeting obligations does not require 100% accurate eDiscovery. 100% accuracy could call for a double review, or double the data collection which only places more burden on the review team and increases costs for the client.
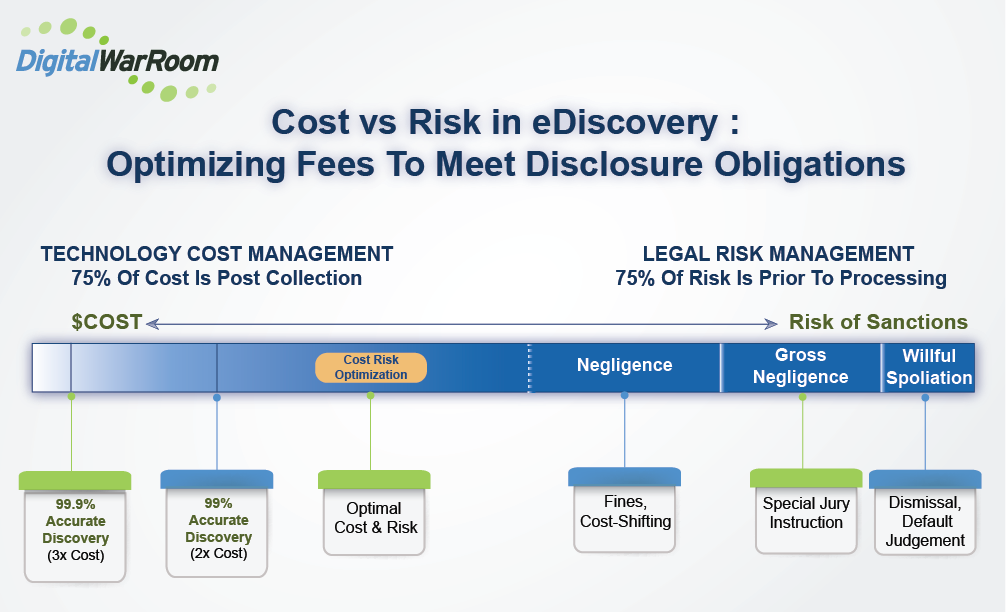
Risk of Sanctions
What are steps you should take to meet and go beyond your requirements?
Manage Legal Risk Across the Entire eDiscovery Process
Manage Legal Risks Related to Security
Law firms are among the top target for Ransomware attacks. Ransomware is a type of malicious software designed to block access to a computer system until a sum of money is paid. Even when a firm pays the sum, there is no guarantee that data will be returned and protected. One recent malicious attack has involved posting the name of the attacked firm on a public website, asking for $1 million to remove the name from the site and return the data. When the firm paid the sum, the attackers asked for another $1 million or they would release the data. There are several important measures we recommend to protect against such attacks.
FRCP 1 requires matters be handled in a manner that is “just, speedy and inexpensive.” Having a budget will be important for discussions with not only your client but also the Court should issues arise about proportionality or eventual final cost awards.
Manage Overall Litigation Budget
Hosted eDiscovery Software Costs
Desktop eDiscovery Costs
Training and Support

© 2002 - 2024 Digital WarRoom All Rights Reserved


I hope you enjoy reading this blog post. I hope you enjoy reading this blog post.