CHAPTER 4: THE CHECKLIST MANIFESTO
Given all the discussion in the section above, it is my firm belief that the best way to proceed in handling eDiscovery matters is to have checklists for each step of the process. The eDiscovery Checklist Manifesto (EDCM) is a complete workflow for the steps every legal professional should consider as they conduct litigation and eDiscovery.
This guide was updated by Bill Gallivan, the Managing Director at Digital WarRoom and the most current iteration of the document can be found on the DWR web site at: https://www.digitalwarroom.com/ediscovery-checklist-manifesto
Likewise, our EDCM diagram represents a conceptual iterative process. One might repeat the same step numerous times, homing in on a more precise set of results. One might also cycle back to earlier steps, refining one’s approach as a better understanding of the data emerges or as the nature of the matter changes.
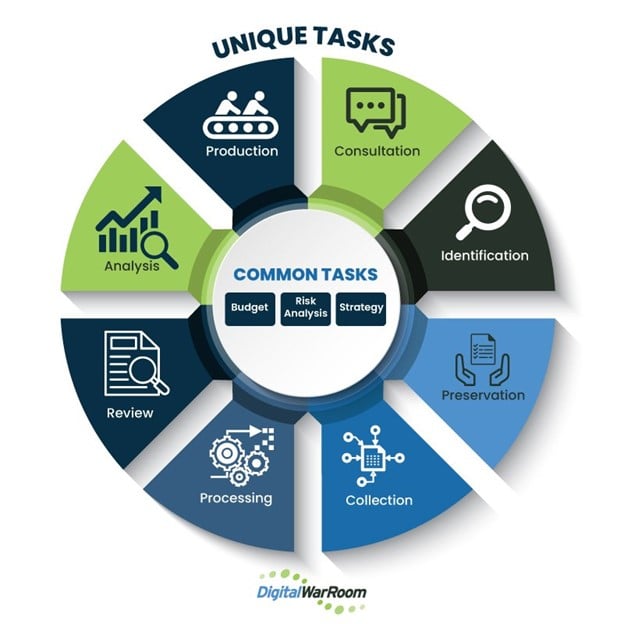
The outer circle represents the generally prevalent common steps which may occur in the eDiscovery process while the inner circle represents more unique common steps which may occur at any point in the process.
The diagram is intended as a basis for discussion and analysis, not as a prescription for the one and only right way to approach eDiscovery.
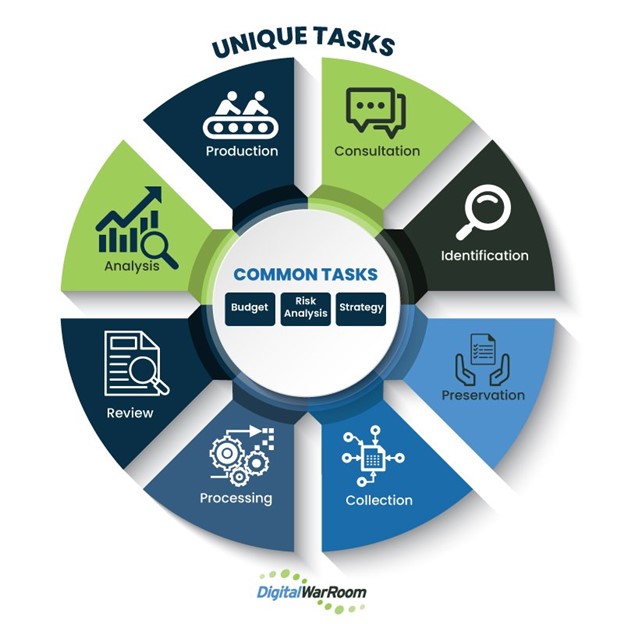
The eDiscovery Checklist Manifesto (EDCM)
SPECIFIC UNIQUE STEPS
- Client Consultation: Points to consider and discuss in the initial client meeting
- Identification: Identify and validate potentially relevant ESI sources
- Preservation: Prevent potentially relevant data from being destroyed after litigation becomes apparent.
- Collection: acquisition of potentially relevant ESI as defined in the Identification phase.
- Processing: Electronically prepare ESI for review
- Review: Search, examine, and assess processed ESI
- Analyze: Detailed examination and scrutiny of reviewed ESI
- Production: Proposed formats & methods
COMMON STEPS
- Strategy: Comprehensive game plan for controlling your litigation
- Risk Analysis: Cost vs risk analysis of case
- Budget: Contemplated costs & damage assessment
UNIQUE STEPS
CLIENT CONSULTATION
There are consultation points that every attorney should cover or consider in the initial discussion with client. These may refer to the EDCM steps such as ID, Preservation, and Collection.
Consultation can occur at any time but should occur before any specific litigation to adequately prepare the client in a proactive manner for issues that may arise should litigation occur. Consultation may then occur cyclically throughout any specific project and will flow into the Strategy checklist set out further below.
IDENTIFICATION
In the EDRM process, the legal team uses the identification phase to develop and execute a plan to identify and validate potentially relevant ESI sources including people and systems.
The scope of this data may be uncertain in the early phases of a legal dispute and may change as the litigation progresses. But learning the location of potentially discoverable data is necessary to issue an effective legal hold in the Preservation stage.
PRESERVATION
Keep in mind, however, that the duty to preserve relevant data does not always flow from a litigation hold notice. It may arise under a common law obligation or under a statute or regulation. The Committee Notes to FRCP 37 (e) state, in part, “Many court decisions hold that potential litigants have a duty to preserve relevant information when litigation is reasonably foreseeable. Rule 37(e) is based on this common-law duty; it does not attempt to create a new duty to preserve.”
In the federal and most state courts, there is no tort cause of action for the intentional destruction of evidence after litigation has commenced. [1] But since such destruction constitutes abuse of the discovery process, it is subject to a broad range of sanctions. These sanctions are, however, intended to remedy discovery abuse, not to punish the offending party.
INTERVIEW CUSTODIAN
Identify and review all custodians who may be relevant to the litigation. Simple and straightforward questions often elicit the most helpful answers and should be focused on the time frame and data questions at the center of the dispute.
COLLECTION
Collection is the acquisition of potentially relevant electronically stored information (ESI) as defined in the Identification phase. The process of collecting ESI will generally provide feedback to the Identification function which may then influence or even expand the scope of the eDiscovery project.
Keep in mind that collection is NOT the same as preservation, which is described above. Collection is the first step in the ultimate review process and should be done subject to some specific review goal. Collection processes may be in person or remote and typically account for roughly 13% of the entire cost of an eDiscovery project.
PROCESSING
After collection, it is often necessary to “process” data to prepare it for review. This involves machine-based manipulation of all the various data sets collected into a common format for use in a software review tool.
REVIEW
Document review is a critical component in the eDiscovery process and is used to identify, classify, categorize, and prepare for production a variety of document types. Most analyses of the eDiscovery process agree that this is the most expensive step in that process and can often account for as much as 70% of the eventual spend. Given that pricing prominence, it is critical that this stage be handled efficiently.
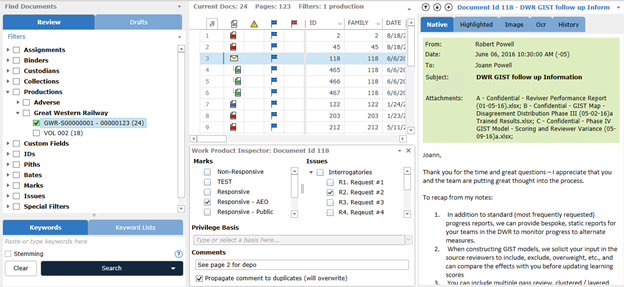
Review Panel: Filter Tree, Result List, Document Browser
ANALYSIS
In the original EDRM model, analysis was a standard function of the Review process and was primarily manual. But as more sophisticated analytics tools have emerged, this phase has drawn more attention as an area to increase productivity.
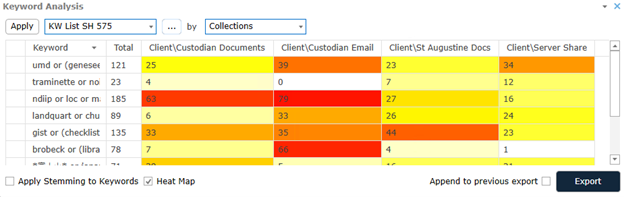
Keyword Analysis - Hits by search string
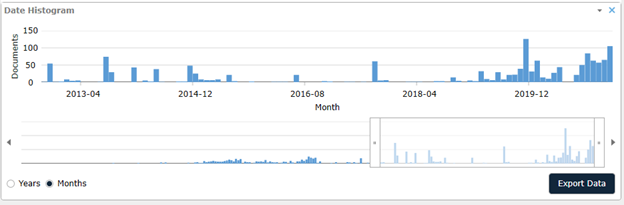
Date Analysis - Looking for gaps
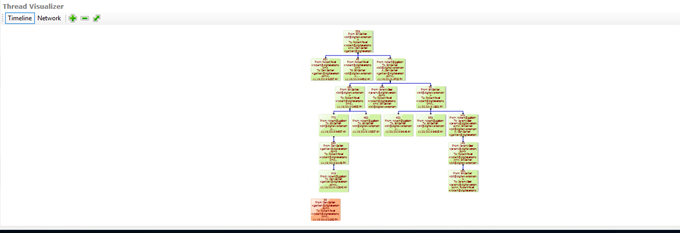 Thread Visualizer - Review only the longest threads
Thread Visualizer - Review only the longest threads
PRODUCTION
The production of ESI continues to present significant challenges in the discovery process. FRCP Rule 26(f) posits that the method and format of production shall be included in the discovery plan.
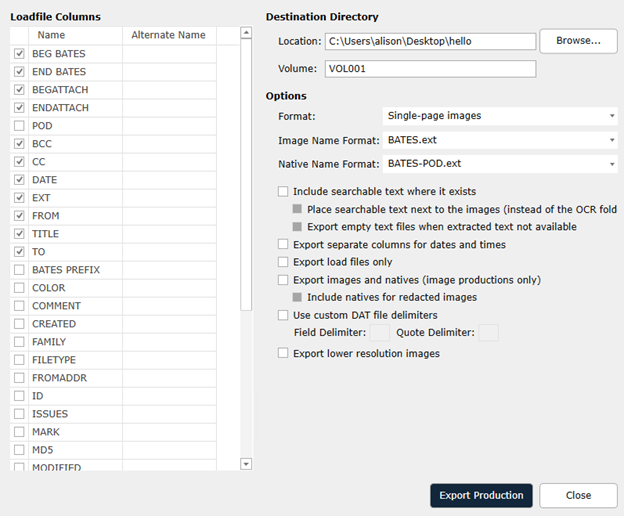
Structured Productions - Load-file wizard
COMMON TASKS
These common tasks fall generally under the heading of Project Management. For a greater consideration of that topic, the author recommends that you read Project Management in Electronic Discovery: An Introduction to Core Principles of Legal Project Management and Leadership by Michael I. Quartararo.
BUDGET
FRCP 1 requires matters be handled in a manner that is “just, speedy and inexpensive.” Having a budget will be important for discussions with not only your client but the Court when discussions arise about proportionality or eventual final cost awards.
RISK ANALYSIS
DWR has long been centered on risk analysis as a key component of their strategic approach to eDiscovery, not just in weighing relevant eDiscovery obligations but also exploring methods of managing cost vs risk.
Tom O’Connor and Bill Gallivan have discussed that balance in webinars as well as a live presentation at the ABA TechShow 2020. A slide from that presentation is shown below and the entire presentation can be viewed at https://www.digitalwarroom.com/webinars.
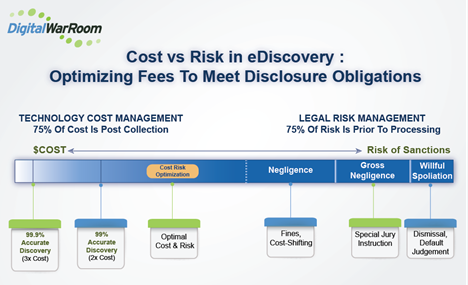
Balance Legal Risk and Budget Risk
STRATEGY
A comprehensive strategy will be the single greatest factor in controlling your litigation. It should be dynamic, flexible, and reviewed periodically.
Once you have completed the various steps specific to your process in the EDCM checklist, you will be ready to proceed to using software to perform those tasks. The following section will illustrate how we accomplish that using Digital WarRoom.
[1] There are exceptions. In Ohio, for example, a Court found that Ohio is one of the few jurisdictions that recognize an independent tort of intentional spoliation of evidence, and its elements are:
(1) pending or probable litigation involving the plaintiff,
(2) knowledge on the part of the defendant that litigation exists or is probable,
(3) willful destruction of evidence by the defendant designed to disrupt the plaintiff’s case,
(4) disruption of the plaintiff’s case, and
(5) damages proximately caused by the defendant’s acts.
-1.png?width=400&height=164&name=DWRLogoClassic%20-%20Copy%20(2)-1.png)








Comment On This Article