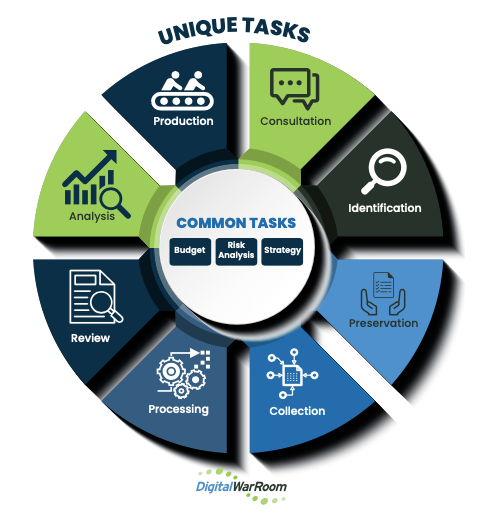
A Model to visualize the workflow
The outer circle represents unique steps in eDiscovery workflow while the inner circle represents more common steps which may occur at any point in the process. The ordering of the stages is important conceptually; you will likely cycle back to different steps as needed, refining your approach as you gain a better understanding of the data or as the nature of your matter changes.
Attorney Obligations
Attorneys must comply with:
- Federal and State Rules (FRCP 26(b)(1), 26(f), 34).
- Tech Competency Standards (ABA Model Rule 1.1).
- Local Rules and ongoing client communication.
They must meet ethical obligations of competence, communication, and proactive management.
Client Interview
The first consultation sets the foundation for the case. Attorneys should ask about:
- Business type and practices (document types, technology, data management).
- Information governance (retention policies, DMS).
- Legal preservation requirements (HIPAA, banking, privacy laws).
- Data mapping and employee org charts.
- Privacy, insurance, and risk considerations.
This stage manages client expectations and develops an actionable project timeline. You will also be defining the SCOPE OF YOUR DOCUMENT REQUEST and the DOCUMENTS YOU WILL NEED TO PRODUCE IN RETURN.
*Contact Support@digitalwarroom.com if you have questions or would like assistance asking your client where to find potentially relevant data. Billable Service if we interact with your client at $315/hour.
Identification
This phase identifies relevant ESI (Electronically Stored Information) sources. Attorneys must:
- Have your client create a data map of servers, devices, storage systems, archives, and BYOD devices such as phones and tablets.
- Consider hardware, software, communication tools, and departmental data.
- Link custodians to data sources via org charts.
*Contact Support@digitalwarroom.com if you have questions or would like assistance defining sources or potentially relevant data from your client. Billable Service at $315/hour when we work with your client’s IT department.
Preservation
The duty to preserve arises when litigation is reasonably anticipated. Core principles:
- Prevent destruction of potentially relevant data.
- Implement litigation holds (legal notices suspending normal deletion).
- Communicate with custodians, reissue holds as needed, and maintain audit trails.
- Remember: preservation is broader than production.
When processed into DWR, your data is subject to forensic fingerprinting and audit to ensure defensible preservation.
Define the Scope and Form of Production
Custodian Interviews – Build Legal Strategy
Interviews establish what custodians know and what data they hold. Areas include:
- Job duties, system access, devices, email accounts, backup practices.
- Identifying relevant folders, colleagues, and confirming accuracy.
- Written notifications and audit trails.
eDiscovery ESI Agreements and Protocols
Draft or negotiate an ESI email to receive and Deliver Documents of interest
*Contact Support@digitalwarroom.com for free advice.
For Context, look at some sample ESI Agreements and demand emails.
Scope of production – define what is relevant to the dispute:
- Define Custodians of interest,
- Agree on types of data – email, text, phones, financial database reports, etc.
- Agree on responsive Keywords, keyword strings, and Boolean searches that capture relevant documents.
- Agree on relevant date ranges
- Allow for rolling productions
Form of production - agree on how you will exchange relevant documents.
Production of ESI requires strict protocols:
- Formats (native, TIFF, PDF, text, databases).
- Sample loadfile testing to align metadata fields.
- Privilege and redaction protocols.
- Delivery methods (FTP, file share, hard drive).
- Scheduling, communication, and validation plans
- Metadata: Metadata describes attributes of files (who, when, where, how). Types include:
- Descriptive, structural, administrative, reference, statistical, system, application, and vendor-added metadata.
- Attorneys must identify relevant metadata and understand variances by file type.
Email Example of Metadata demand for the form of Production:
- BEGBATES
- ENDBATES
- ATTRANGE (BEG ATTACH END ATTACH)
- BEGATTACH
- ENDATTACH
- PAGECOUNT
- CUSTODIAN
- TITLE / SUBJECT
- THREAD
- FROM
- TO
- CC
- BCC
- SENT
- RECEIVED
- AUTHOR
- CREATED
- MODIFIED
- FILEPATH
- FILENAME
- FILESIZE
- FILEEXT
- NATIVELINK
- OCRPATH
*Contact Support@digitalwarroom.com for free advice. We will help you construct your ESI Protocol email or agreement as an included service.
Customer Collection after Preservation
Collection involves defensible acquisition of ESI:
- Methods: self-collection, archiving tools, or forensic experts.
- Documentation and authentication are crucial.
- Audit trails and agreements with opposing parties ensure defensibility.
- IT IS ALWAYS BEST TO COLLECT ELECTRONIC DOCUMENTS, EMAIL, TEXTS IN NATIVE FORMAT TO PRESERVE METADATA.
* Contact Support@digitalwarroom.com to get free advice on the best format for processing into Digital WarRoom.
Upload Files/Documents and Process into DWR
Processing prepares data for review.
Contact Support@digitalwarroom.com for an upload link to deliver to your proactive support professionals, clients, or the opposing party (incoming Productions)
- Organize and create folders in the DWR application process tab.
- Drag and drop collections of data into the process folders from the XFER upload folder
- DWR will automatically expand the contents of mailboxes, zip files, and structured productions; populate searchable tables of metadata and create indexes for keyword searching; log exceptions.
- Apply global filters with the Policy Filter for de-duplication, dates, keywords, and file-type exclusions.
- For incoming third-party productions: Examine and confirm metadata overlay when importing load files. Quick reference guide for importing third-party productions.
Importing data into DWR for review makes use of wizards to guide you, maintain audit trail, and ensure forensic integrity
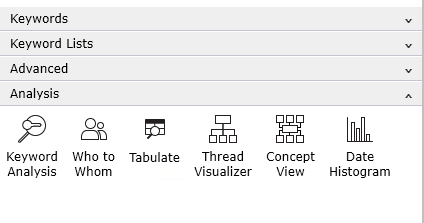
Review Tab: Analysis in DWR
Analysis is continuous throughout the case. DWR has many analysis tools with documented in the user guide. Use this link for a quick overview or contact Support@digitalwarroom.com and allow us to walk you through the options.
- Data Assessment: evaluate size, file types, custodians, and random samples.
- Email Analysis: map threads, visualize communications, analyze PSTs.
- Document Analysis: review extensions, identify gaps in timelines.
- Content Analysis: enhance searches, extract facts.
- Project Management: track costs, processes, and litigation readiness.
- Settlement Analysis: identify key documents influencing negotiations.
These tools are located on the Analysis tab in Review
You may conduct analysis on any subset, or all your data. You may export analysis results in DWR to share with your clients, collaborate with experts, or use in negotiations with adverse parties.
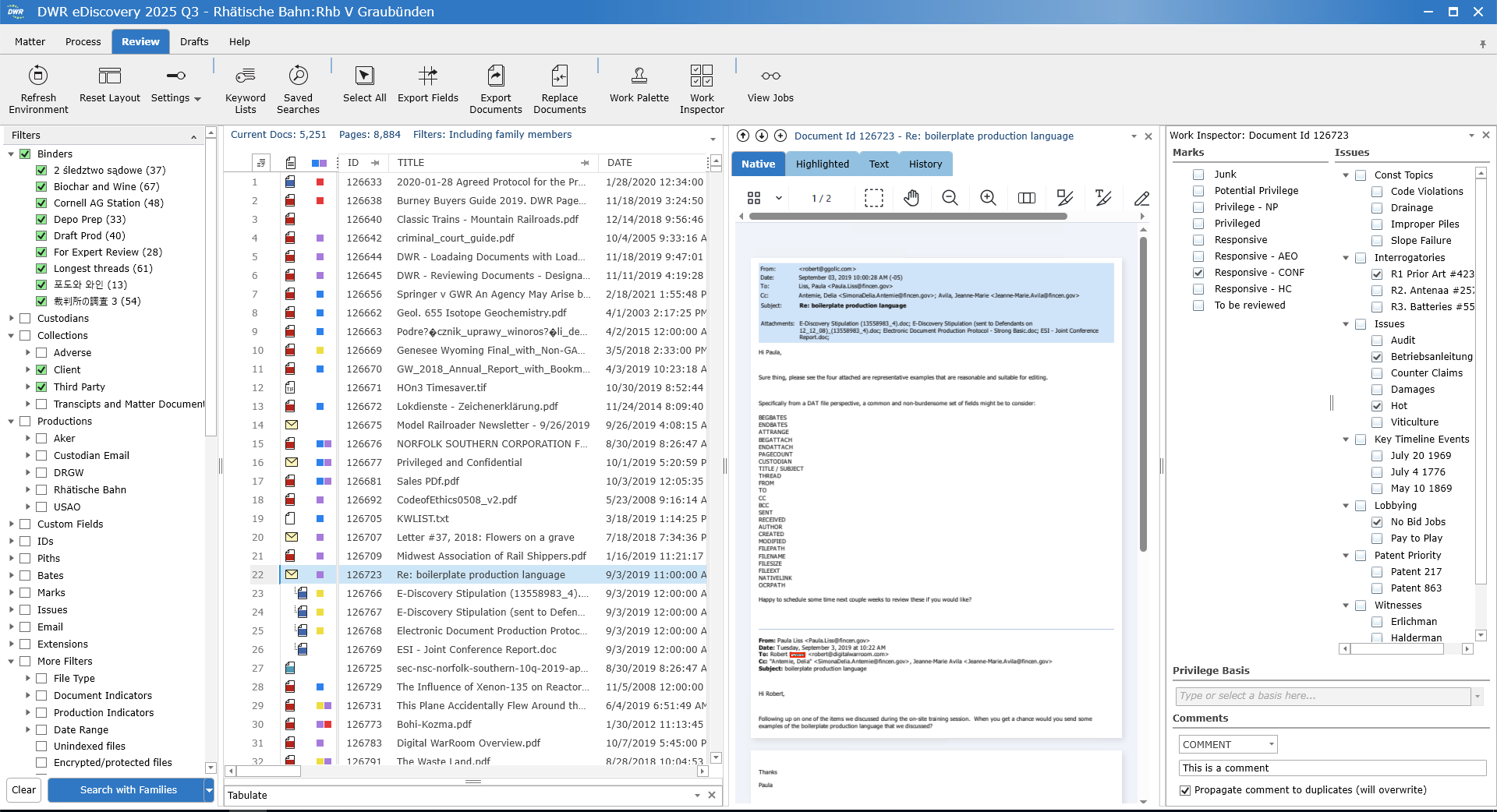
Document Review in the DWR Review Tab: Find documents to Use and Produce
Review is the costliest stage (60–70% of eDiscovery expenses). Attorneys should:
- Assign documents, assess responsiveness, and fit them into case outlines.
- Implement QC protocols to avoid errors or repeat reviews.
- INDIVIDUAL REVIEW TRAINING IS ALWAYS INCLUDED IN YOUR SUBSCRIPTION.
Contact Support@digitalwarroom.com to learn how to mark and issue code documents, organize documents, create binders for depositions, experts or exports, prepare your documents for production. Among the many areas of included support and training are:
- Matter Settings
- Filtering and Searching Documents
- Applying Work Product – Marks, Issues, Comments, Privilege Basis
- Saving Results to Binders or Draft Productions
- Keyword Searching
- Keyword Lists
- Exporting Fielded Data and Document Indexes
- Exporting Documents
- Replacing Documents in Review
- Email Filtering
- Thread Visualization
- Work Product Inspector / Palette features
- Working with Assignments
A typical DWR Review is shown below – with the filter options on the left; result list or grid of documents in the center left; document browser illustrating the selected email currently under review on the center right; most right pane is the work inspector. You can customize the display to best meet your review needs, and span across multiple monitors.
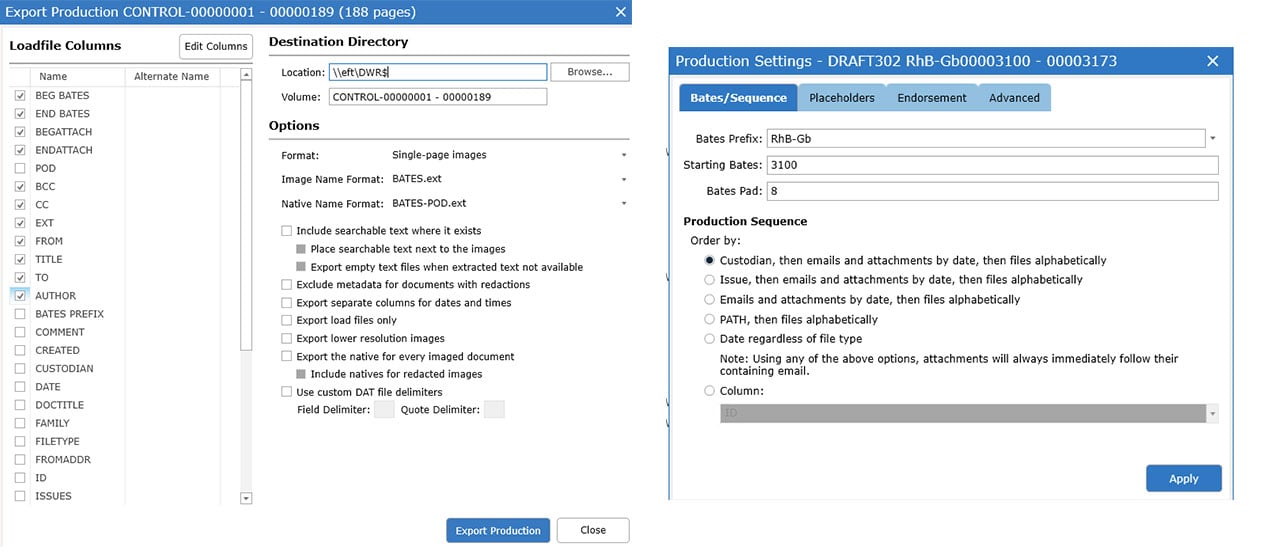
Production – Draft Tab
Once you have tagged, blindered, or otherwise identified (i) what you want to produce (scope of Production) and how you want to produce the documents (form of Production), use our Production wizards in the Draft to create your Production and deliver your Production.
In Drafts, work is done to collect, manage, and produce a set of reviewed documents for delivery to the requesting party.
There are four steps in the Drafts to complete a production; this workflow remains the same whether working with 10 documents or 10,000 documents: Create, Prepare, Endorse, and Finalize
- Prepare Production: Documents being produced in an image format are converted to PDF and documents produced as natives are indicated in the production set. You have several settings that can be configured to align to your ESI agreement and production specifications.
- Endorse: Bates numbers, Protective Order Designations (PODs), and redactions are burned onto static images. Placeholder image created for documents being produced as native or withheld.
- Finalize: Checks are completed for any errors, and the production set is sealed.
- Abandon: Remove the production set and reset any Bates numbers applied.
- Production Settings: Select the settings for the production set.
- Export Production: Build your load files IAW the ESI agreements and export to a folder for delivery to the requesting party.
Illustrated below are samples of two DWR production wizards – the sturctured export on the left, and the production settings on the right
Strategy
Litigation strategy must be flexible and case-specific:
- Define scope, venue, deadlines, witnesses, and data types.
- Consider arbitration, agency involvement, or social implications.
- Develop co-counsel strategies and project management workflows.
- Determine resources, vendor selection, and software.
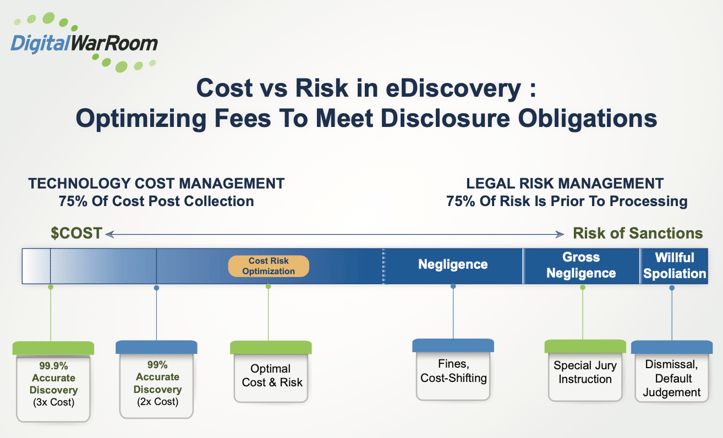
Risk Analysis
Balancing costs and risks is central:
- Most costs occur post-collection; most risks arise pre-processing.
- Sanctions for spoliation include fines, adverse instructions, dismissal, default judgment.
- Use defensible review hours, privilege logs, keyword analysis, and audit trails.
- Apply risk-adjusted decisions (e.g., bulk marking) carefully.
Budget
Budgeting aligns with FRCP 1’s mandate for “just, speedy, and inexpensive” resolutions:
- Consider costs, damages, venue awards, insurance, and arbitration.
- Use calculators to estimate attorney hours, ESI volume, and hosting costs.
- Provide budget transparency for clients and courts.
Conclusion
Use Support@digitalwarroom.com early and often.
The Digital WarRoom eDiscovery Checklist Manifesto presents a longer, structured, practical approach for litigators navigating modern discovery, emphasizing:
- Attorney competence in technology and law.
- Proactive client engagement.
- Defensible, auditable processes for preservation, collection, and review.
- Continuous analysis, risk management, and cost control.
- By integrating strategy, risk, and budgeting into every phase, attorneys can meet ethical and procedural obligations while minimizing costs and maximizing defensibility.
-1.png?width=400&height=164&name=DWRLogoClassic%20-%20Copy%20(2)-1.png)








Comment On This Article