Most attorneys representing businesses in litigation have experienced the excruciating burden of reviewing ESI - e-mails and electronically stored information - for privilege or work-product protection, and then having to create a privilege log, a laborious manual effort to build a list describing each document withheld for reasons of privilege. Counsel agonizes over the communications involving the client’s counsel and then the adequacy of the description of the withheld documents in the privilege log.
The Top 2 Key Concerns Among Litigators And eDiscovery Professionals In The Area Of Privilege
1. How can we hold down the cost (and onerous burden) of managing privileged content? The preparation, review and editing of a detailed Privilege Log is a painful manual experience for many paralegals and litigation support teams.
2. Fear of the Risk of inadvertent waiver of privilege, and a need to understand available remedial actions, should inadvertent production occur.
It’s easy to find articles, surveys and papers published in litigation and e-discovery field that call out concerns about the high cost of pretrial discovery of email and other digital content. While the FRCP rules leave room for the courts to relieve a party from the requirements of providing a privilege log due to undue burden or expense, new e-discovery technologies and applications are actually making the process of managing privileged documents and creating the privilege log a less burdensome, (almost automatic!) task.
The first section of this blog lays out 10 key considerations for effectively managing the process of identification, review, and annotation of privileged content. The second section briefly outlines the privilege management support features in Digital WarRoom e-discovery software, and provides an example of a privilege log.
The concept behind Digital WarRoom is to minimize duplicative effort. The essential information desired or required in a privilege log results directly from the searches, tagging decisions, and privilege annotation content created by review attorneys in the course of document review. Digital WarRoom simply captures and leverages that activity trail to automatically generate the privilege log.
The points below highlight key considerations for managing, reviewing, and reporting on privileged documents. The information is based on our 20 years experience in managing e-discovery projects, and while valuable, it’s not an exhaustive guide; “your mileage may vary” – be sure to work cooperatively with the courts and opposing counsel to define your path.
1) Know The Rules Governing Privilege
Federal Rule 26(b)(5)(A), governing the disclosure of details describing documents withheld for reasons of privilege, traditionally has required a document-by-document list containing the following information at a minimum:
(i) type of document (e.g., letter, e-mail, or memorandum);
(ii) general subject matter of the document;
(iii) date of the document;
(iv) author of the document;
(v) addressee of the document;
(vi) other recipients of the document; and
(vii) where not apparent, the relationship of, the author, addressees and recipients.
If your case is coming before state or local courts, investigate and understand the rules, case law, and decisions in your jurisdiction. Some state and local courts have adopted more detailed rules on privilege, based on the federal rules. For an example, see Local Rules of the United States District Courts for the Southern and Eastern Districts of New York 26.2(a)(2)(A).
2) Plan Ahead: Address Privilege Issues in a Meet & Confer
Parties should meet and confer early in the case, as part of their initial discussion about document production, before or at the Rule 26(f) conference, to discuss: (1) the volume of claims of privilege or protection the parties anticipate encountering, (2) how to segregate and exclude presumptively privileged or protected documents from production, and (3) how to handle the inadvertent production of privileged or protected material. Counsel should take advantage of Federal Rule of Evidence 502 (see claw back agreements, below) by agreeing early in the case that the production of privileged or protected documents will not result in any waivers.
3) Agree On Privilege Log Deliverables
Parties should negotiate early and come to agreement on the form and the level of detail the privilege log needs to contain. Some time-saving alternatives include, but are not limited to:
- Agreeing on categories of exclusion
- Limiting metadata to a few key fields
4) Key Word Search / Identifying Potentially Privileged Content
Early in the process, counsel and e-discovery team should develop a list of search terms to identify potentially privileged documents. Consider and decide on specific treatment for e-mail threads and attachments (sometimes referred to as ‘family groups’). A clear protocol regarding the identification and annotation of privileged documents will improve accuracy and help avoid failure to identify or tag privileged content as such.
5) Document Review: Develop A Privilege Management Workflow
Entire books have been written about the various decisions involved in developing an e-discovery workflow that serves the case strategy, client needs and budgets, and available time and resources. The following are but a few of the elements that counsel should consider, in consultation with the e-discovery service provider if needed, in making workflow decisions related to privileged content.
Gain efficiency with pre-defined Privilege Annotation Comments
When selecting an e-discovery review tool, look for the ability to create a list or library of privilege text annotations. These can be crafted by Counsel at the outset of the matter, and should be available to reviewers for selection and association to a document, during the document review phase, and to Privilege and QC Reviewers on subsequent tiers of review. The selection of a standard annotation should then be customizable, allowing additional editing or addition of reviewer comments.
Assure Consistency with Mark Propagation
Choose an e-discovery review program that has the capability to identify duplicate or near-duplicate documents. In combination with Privilege term search, his capability can be utilized to rapidly identify batches of documents that are highly likely to be responsive or privileged.
In Digital WarRoom, a ‘digital fingerprint’ identifies duplicates within the corpus. When the first review occurs on a given document, a pre-configured option will cause all existing duplicates to be automatically marked consistently with the first, eliminating errors and reducing review effort. This is accomplished via a Digital WarRoom feature described as ‘Mark Propagation’ – (ie; propagate an original decision across all duplicate occurrences of the same document.)
Exceptions to Mark Propagation: Consider Situational or Contextual Privilege
Mark Propagation can be a great time saver, and can reduce risk of errors. However, there may be situations when counsel will have more subtle distinctions on which to decide, tag, and track responsive vs. privileged documents.
When evaluating an e-discovery software program, consider the handling of attachments and email conversations (related emails, sometimes called ‘threads’). Attachments to e-mails should be identified as attachments. They should exist independently of the parent document, yet retain the association to the parent. (Sometimes called a ‘family group). This model provides the greatest flexibility to support counsel decisions on handling review and production of documents. An effective e-discovery review system should provide support for reviewing/tagging/producing - or alternately, logging for privilege - documents in their original family groups, OR as individual documents.
While Mark Propagation realizes greater consistency and cost savings in review, there may be situations when in fact, the duplicate of a privileged document may not be deemed privileged.
Consider this example:
The review document set may contain a privileged email correspondence between client and attorney that has an attachment in the form of a Word document that would not be considered privileged on its own.
A duplicate copy of that Word document attachment may reside elsewhere within the document set. Counsel might decide that the email + attachment described first should be withheld according to privilege. Counsel might also decide that the standalone duplicate of the Word document is not privileged and should be produced. In this example, the ‘same document’ is privileged in one instance due to its context, and deemed responsive in the second instance. This is a decision for counsel to make, and perhaps to negotiate up-front in the ESI agreement.
Another view counsel may take is that each document, regardless of family associations, should be considered on its own. Although an e-mail may be designated privileged or protected, it does not necessarily follow that the attached document is privileged or protected. Therefore, Counsel may decide that each individual message or document should be reviewed and logged separately if deemed privileged or protected. This is a key consideration for review planning and ESI agreement negotiation. It’s a good reason to involve your e-discovery service provider early in the process, so that the workflow can make best use of the features and capabilities of the e-discovery review software program. Whatever the decision or agreement might be, Digital WarRoom can support counsel decision with an efficient solution.
6) Include Quality Control And Auditing In The Workflow
Quality of Review
The review workflow should include QC steps to verify the accuracy and thoroughness of privilege identification. This verification can be done via sampling, but the sample, whether random or systematic, should be of a sufficient size and variety so that the results will be valid. Depending on the case, strategy, and document mix, the decision is sometimes made to conduct a QC review on 100% of documents identified for production.
Defensibility of the Process
It’s advisable to keep track, in written form, of the efforts made to search for privileged or protected documents. If the assertion of privilege or protection should be challenged, counsel may have to demonstrate to the court that reasonable steps were taken to identify privileged or protected communications. This is difficult however, without some automated tools.
In Digital WarRoom, the system keeps a detailed audit log of every batch process, every search run (including the search terms), and every document tagging decision, along with reviewer identification and the date of decision. In Digital WarRoom, these audit logs are created automatically in the background, requiring no extra effort on the part of the review team. Audit trails and reports are readily available should counsel be challenged to defend the process.
7) Address Redaction Management In the eDiscovery Workflow
Sometimes the managing attorney may wish to track and report on redacted documents – essentially ‘partial privilege’ items.
Like a document that is privileged or protected in its entirety, e-discovery software should allow you to track and report on documents containing redactions. Look for the ability to create a list of redacted documents (with Doc ID, to/from, title or subject, and other important metadata fields).
Digital WarRoom supports this process, and allows export of the list of redacted documents to Excel, where it can be further annotated or formatted for reference by the case team or production to the courts.
8) Clawback: A Course Of Action In the Event Of Inadvertent Production
A huge concern of litigation and e-discovery teams is the potential for inadvertent waiver of privilege occurring via a document production error. This can occur if, for example, a reviewer tags a document as responsive when in fact it should be held back as privileged.
Federal Rule of Evidence 502(b) states that disclosure of privileged documents in a federal proceeding or to a federal office or agency will not constitute a waiver in a federal or state proceeding where (1) the disclosure is inadvertent; (2) the holder of the privilege or protection took reasonable steps to prevent disclosure; and (3) the holder promptly took reasonable steps to rectify the error, including, if applicable, following Rule 26(b)(5)(B) of the Federal Rules of Civil Procedure.
Accordingly, Rule 26(b)(5)(B) provides a procedure for a party to assert a claim of privilege or protection after production. In the event of inadvertent production, the party asserting privilege or protection must give notice to the receiving party of the claim and the basis for it. The notice must be sufficiently specific to permit the receiving party to evaluate the claim of privilege or protection. The receiving party, after notice, “must promptly return, sequester, or destroy the specified information and any copies.” This is referred to as a “Clawback”.
In the digital world of e-discovery document review and production, claw backs can be problematic. Be sure to use an e-discovery software review system that will efficiently manage the claw back process, and ensure that a privileged document, once clawed back, is prevented from being released again in a future production.
Digital WarRoom has a strong claw back feature. If it is discovered that a document intended to be held as privileged was inadvertently produced, or is in a draft production about to be produced, that document can be removed from the production folder in Digital WarRoom.
Once clawed back, the document can then be re-tagged as privileged, which would prevent it from future production. As an extra measure of safety, documents carrying a ‘Clawed Back’ mark, or their duplicates, will provide a warning message at time of production, allowing the operator to remove them from the production.
Bonus: Highlights Of Privilege Management Features In Digital WarRoom
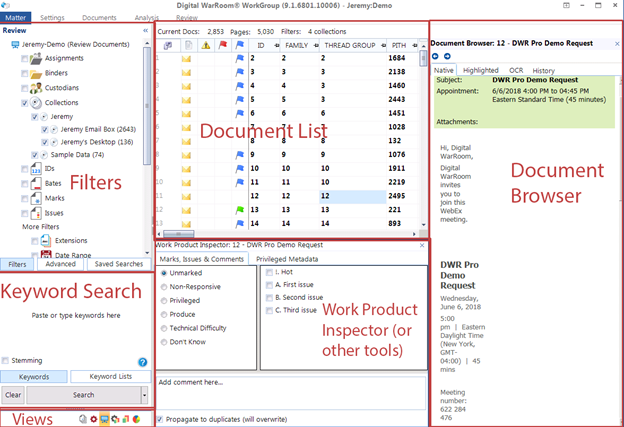
A user-friendly interface displays document detail along with a work product palette, so privilege can be ascertained, tagged and annotated in a single view. This screenshot shows the full Digital WarRoom interface which offers flexibility in showing/hiding different tools and views as well as docking these views to your preferred location/orientation. The bottom-center panal shows the Work Product Inspector, where you can apply work product to the currently selected document. For example: mark documents, as produced, privileged, etc.
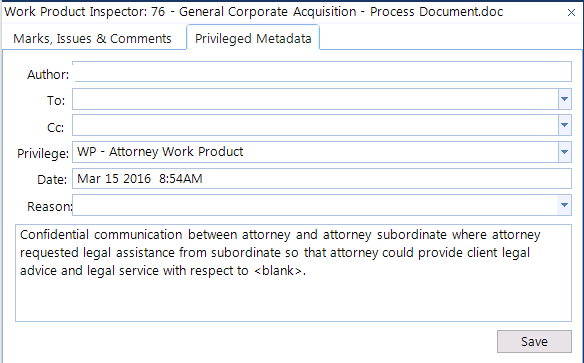
Within the Work Product Inspector, you can tab over to the "Privileged Metadata" tab to fill out our privilege log for an individual document on the flying during document review.
Conclusion
With up-front planning and a consistent review protocol, the process of document review can capture all the important information needed to create an accurate, detailed and defensible privilege log – automatically. Of course, each case has its own unique challenges. Digital WarRoom was designed to be flexible enough to meet special requirements. The consultants at Digital WarRoom are e-discovery experts and the creators of the Digital WarRoom e-discovery technology, and will be glad to assist in creating and monitoring effective privilege management processes.
-1.png?width=400&height=164&name=DWRLogoClassic%20-%20Copy%20(2)-1.png)









Comment On This Article